
Unseen Risks, Uncovered!
The Affordable Way to Secure
Your Business
Our security team, integrated with leading technology, brings together environment visibility, attack protection and response orchestration in a single interface, instant to deploy and simple to manage, regardless of security team size and skills.
Just 24 Hours to Full Capabilities!
Rapid time to value with full environment coverage in minutes
Dedicated Security Team
Zero touch protection from common and advanced threats
Compliant with PCI, HIPAA, and GDPR regulatory requirements.
Full service and management - We respond to all threats and alerts
Fixed Price - No Hidden Costs
Coverage from endpoint, user and network-based attacks in a single solution
Do you want protection from internal and external threats, malware, phishing, ransomware and the people behind it to keep you safe?
Your Business Could Be At Risk:
Is Your Business Ready For The DoD’s CMMC Deadline?
Get A FREE 10-Point CMMC Action Plan With A Certified Assessor To Find Out Now:
KEY BREACH PROTECTION CONSIDERATIONS
Deployment
Practice shows that installation issues result in partial deployment leaving parts of your environment exposed. This applies equally both to evaluating existing products, as well as to purchasing a new one. If you have endpoint protection, are there agents installed on all your endpoints? If it’s a network analytic tool, does it cover all portions of your network?
Attack Coverage
Attackers seek weak points in your protection stack and it’s up to you to reduce them as much as possible. Check the protection level your current products provide from each of the three attack types. They might score high against one, but fail against the other. For example, a first class NGAV would dramatically decrease your exposure to Hit and Run\Stay attacks, but would offer little to zero protection against Hit and Expand scenarios.
Management
Breach protection involves multiple workflows: proactive IT hygiene and vulnerability management, triage and prioritize alerts, respond to active attacks and orchestrate the recovery process. Easy and intuitive management of all these functionalities is a must. The competency bar is straightforward – if efficient day-to-day operation of these workflows is beyond the skill of your in-house team, then you’re not secured.
Expertise
At the end of the day, advanced attacks call for advanced skills. You don’t need – and typically can’t afford – employing such skills as part of your team. This need arises regardless of the products you have in place and is especially required when facing a Hit and Expand attack. Skilled analysts are a must to unveil defense-evading malicious presences.
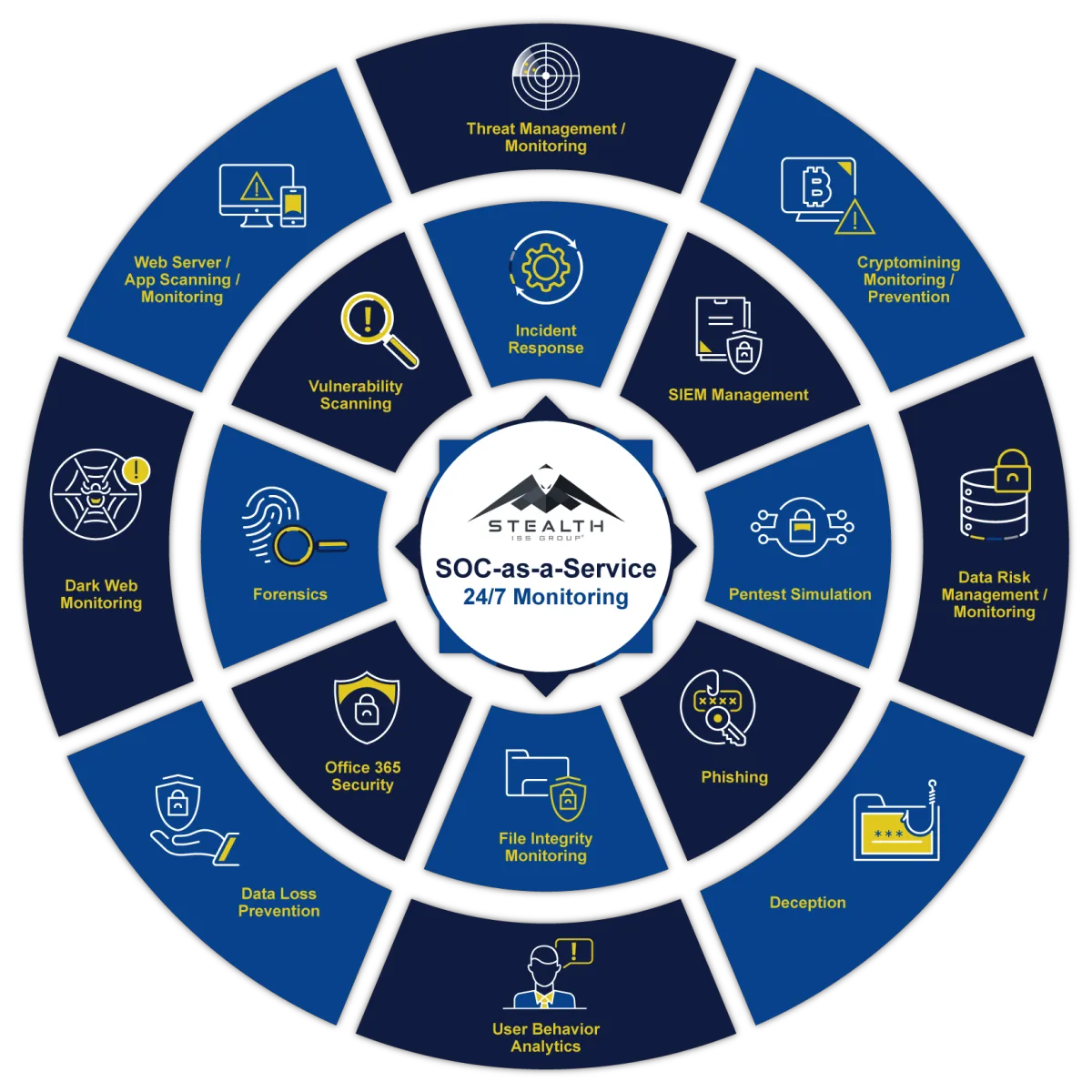
COMPLETE 360 DEGREES OF MANAGED CYBERSECURITY & SOC AT THE COST OF STANDARD ANTI-VIRUS PROTECTION
NextGen AntiVirus (NGAV)
Deception
Endpoint Detection & Response (EDR)
Network Analytics
User Behavior
Response Orchestration

WHY CHOOSE US?
We are your trusted MSSP with the tools and know-how to monitor your IT environment 24/7

SEE EVERYTHING
Extended visibility to prevent & detect threats across your environment
GAIN OVERSIGHT & GUIDANCE
24/7 complimentary MDR service proactively monitoring your environment and providing needed advice
UNDERSTAND CONTENT
Collect and correlate alerts and related data to identify suspicious or problematic activity.
REDUCE SAAS RISK
Ensure your SaaS applications aren’t introducing security risks.

AUTOMATED END-TO-END
Fully automated threat investigation & remediation actions across your environment.
ENJOY AFFORDABLE PROTECTION
All of the protection you need out of the box on a single, fully integrated platform.
PROTECTION MUST BE END-TO-END
Prevention or detection of
an attack's instance is critical,
but it’s only the beginning...

One must assume that the malicious artifact that was identified is the mere tip of an iceberg. Stealth-ISS SOCaaS is the only solution that triggers an automated investigation following each endpoint, user, or network alert, fully disclosing its root cause and scope and applying all the required remediation activities.
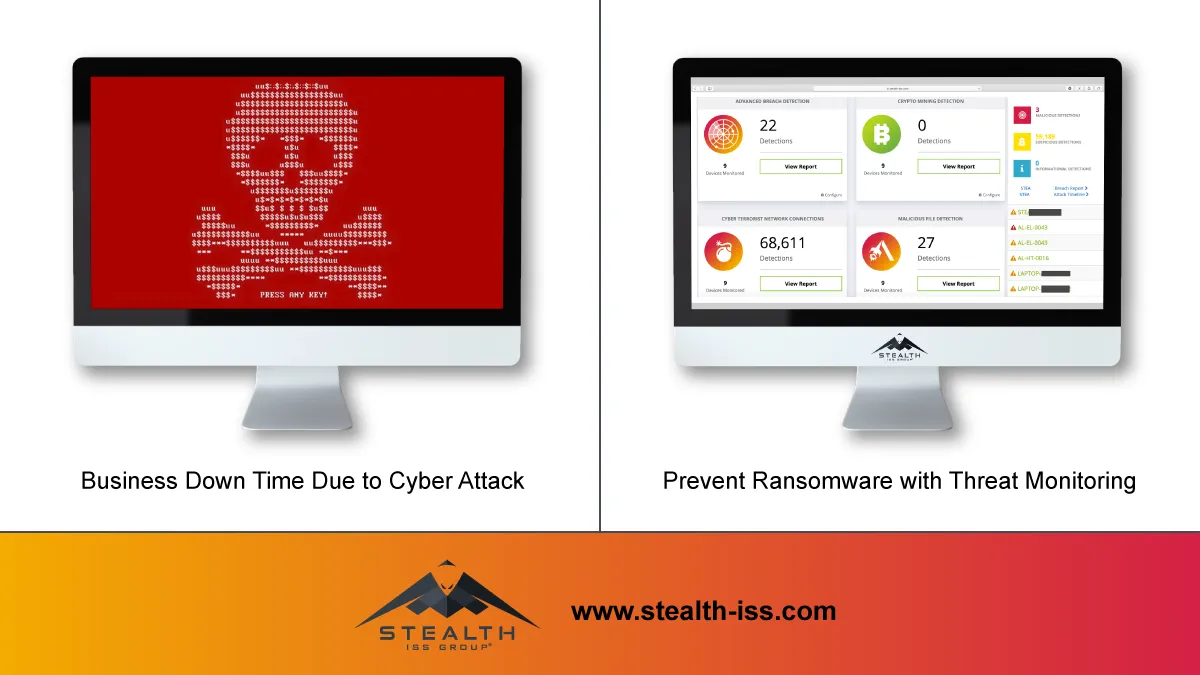
The average time to identify and contain a data breach is 280 days.

60% of small businesses go out of business within six months after a cyber attack.

93% of phishing emails now contain ransomware.
READY TO GET STARTED?

Schedule a meeting with one of our security experts and find out how Stealth-ISS' managed detection and response capabilities can help you.
A successful cyberattack can have devastating consequences, ranging from loss of sensitive data to financial and reputational damage.
Stealth-ISS SOCaaS & Incident Response can help! We'll answer all your questions and provide you with all the information you need to make an informed decision on how to protect your business from threats like cyber attacks, data breaches, and other security risks.
Don't wait until it's too late and your organization has suffered a devastating breach. Take action now by booking an appointment to discuss SOCaaS & Incident Response with our team of experts.
Your organization's security is too important to leave to chance. We look forward to hearing from you soon.

So, what are you waiting for?
Schedule a Meeting with One of Our Security Experts